When you think about security, it’s easy to separate the digital from the physical. You have firewalls and antivirus for your network, and you have cameras and keycards for your building. But in reality, a truly effective security strategy sees them as two sides of the same coin. A modern threat can start online and end with a physical breach, or vice versa. That’s why choosing the right network security company is about more than just IT support; it’s about finding a partner who understands how to integrate all your systems into one cohesive defense. This guide will explain why a unified approach is critical and show you what to look for in a provider who can protect your entire operation, from your servers to your front door.
Key Takeaways
- View Security as a Strategic Partnership: Think of a security provider as an extension of your team, not just a vendor. They offer specialized expertise to manage evolving threats and integrate your physical and digital defenses, allowing you to focus on your core business.
- Vet Providers on Integration and Response: The best technology is ineffective if it doesn’t work with your existing systems or if support is slow during a crisis. Prioritize a provider’s ability to create a unified security system and confirm their specific incident response times and plans.
- Plan for Long-Term Measurement and Growth: Effective security is a continuous cycle, not a one-time project. Create a strategic roadmap that includes ongoing user training, prepares for future business needs, and uses clear KPIs to measure your return on investment.
Why Partner with a Network Security Company?
Managing your own network security can feel like a full-time job on top of your actual full-time job. The landscape of digital threats is always shifting, and the stakes are incredibly high. Partnering with a dedicated network security company means you have a team of specialists whose sole focus is protecting your assets. They bring a depth of knowledge and a suite of advanced tools that are often out of reach for a typical in-house IT department. This partnership allows you to focus on your core business operations with the confidence that your digital infrastructure is secure.
It’s not just about outsourcing a task; it’s about gaining a strategic ally who can help you build a more resilient and secure organization from the ground up. A professional firm can integrate everything from your security camera systems to your cloud defenses into one cohesive strategy, ensuring all your security components work together instead of in silos. They provide proactive monitoring and management, which means they can often spot and neutralize a threat before it ever impacts your business. This level of vigilance is nearly impossible to maintain internally without a significant investment in staff and technology.
Keeping Up with Evolving Threats
Cyberattacks are getting smarter and more complex every day. What worked as a solid defense last year might be completely obsolete today. For most businesses, keeping pace with these rapid changes is a significant challenge. A specialized security partner, however, is always on the front lines. They constantly research emerging threats, update their defense strategies, and understand how to implement a multi-layered security approach. This isn’t just about installing a firewall; it’s about combining technical controls, continuous monitoring, and user awareness to create a robust defense. They can ensure your access control systems are secure from both physical and digital intrusion, giving you a comprehensive security posture.
Understanding the True Cost of a Breach
It’s easy to think of a security breach as a purely technical problem, but the reality is that the consequences ripple through your entire organization. The financial fallout goes far beyond the immediate costs of remediation. You have to account for operational downtime, potential regulatory fines, and the long-term damage to your reputation. If you rely on cloud services, you face another layer of challenges, from insecure APIs to shared vulnerabilities. A single incident can erode customer trust that took years to build. A network security partner helps you understand and mitigate these risks, quantifying the potential impact so you can make informed decisions about your security investments.
The Value of Professional Expertise
A great security partner does more than just sell you software; they provide clarity and efficiency. Instead of juggling a dozen different security tools, an expert can help you build an integrated system that works seamlessly. They can introduce AI-powered solutions that proactively identify threats and streamline your defenses, which significantly reduces the burden on your help desk and internal teams. This expertise is crucial for protecting a modern, hybrid workforce. By integrating physical security technology with information security, a partner provides a holistic view of your operations. They can design and implement foundational systems like fiber network technology solutions that support all your security and operational needs, ensuring everything works together effectively.
A Look at the Top Network Security Companies
When you start looking for a network security partner, you’ll find a mix of global tech giants and specialized local experts. The big names offer powerful, wide-ranging platforms, while local firms provide hands-on integration and support tailored to your specific environment. Understanding what each company does best will help you find the right fit for your organization’s needs. The key is to find a provider that not only offers the right technology but also understands how to implement it effectively within your existing infrastructure. Let’s look at some of the leading names in the industry, starting with a trusted local expert right here in Chicago.
Umbrella Security Systems
As a Chicago-based leader, we specialize in creating unified security solutions that bridge the gap between physical and digital threats. While many companies focus solely on cybersecurity, we integrate it with on-site systems. This means your security camera systems and access control system aren’t just physical deterrents; they become intelligent data sources for your overall security posture. Our approach is consultative. We work with you to design and implement a cohesive strategy that protects your network, your property, and your people, ensuring every component works together seamlessly. This holistic view is crucial for businesses and government clients who need comprehensive, real-world protection.
Palo Alto Networks
Palo Alto Networks is a major player known for its advanced, AI-driven approach to cybersecurity. They are strong proponents of a “Zero Trust” framework, which operates on the principle of “never trust, always verify” for anyone or anything trying to access your network. Instead of offering individual tools, they provide a complete, integrated platform designed to simplify security management. This approach helps businesses protect themselves from sophisticated cyberattacks by ensuring all security components are working in concert, from the network firewall to cloud security and endpoint protection.
Fortinet
Fortinet provides a broad array of cybersecurity solutions and services that protect an organization’s entire digital footprint. They excel at securing everything from individual devices and data to applications, whether they are located in a central office or a remote work environment. One of their standout features is a tool called FortiRecon, which helps businesses see their security weaknesses from an attacker’s perspective. This proactive approach allows you to identify and address potential vulnerabilities before they can be exploited, offering a more comprehensive understanding of your security landscape.
Cisco
Best known for its networking hardware, Cisco leverages its deep industry expertise to offer security solutions that integrate smoothly with your existing network infrastructure. If your organization already relies on Cisco for routers, switches, and other network components, their security products can be a natural fit. This tight integration simplifies management and ensures that your security measures work in harmony with your network operations. Their portfolio covers a wide range of security needs, making it easier for organizations to build and maintain a strong security posture from a single, trusted vendor.
Check Point Software Technologies
Check Point has built a strong reputation primarily on the power and reliability of its firewalls, which serve as a critical first line of defense for your network. Acting as a barrier between your internal network and outside traffic, their firewalls are designed to block malicious activity. Beyond firewalls, Check Point offers a comprehensive suite of security solutions that help organizations defend against a wide variety of cyber threats. Their focus is on providing robust, multi-layered protection that secures everything from the network to the cloud and mobile devices.
CrowdStrike
CrowdStrike is a leader in endpoint protection, which means they focus on securing the devices that connect to your network, like laptops, servers, and mobile phones. Their platform is highly regarded for its threat intelligence capabilities, which help organizations detect, respond to, and neutralize cyber threats quickly and effectively. Instead of just preventing attacks, CrowdStrike’s services are designed to actively hunt for threats within your network. This makes them a strong choice for organizations that need advanced, real-time protection for all their user devices and critical systems.
Microsoft Security
For businesses heavily invested in the Microsoft ecosystem, Microsoft Security offers a powerful and convenient solution. Their security tools are built directly into platforms like Azure and Microsoft 365, creating a deeply integrated defense system. Products like Microsoft Defender provide comprehensive protection across endpoints, email, and cloud applications. The primary advantage is seamless compatibility and centralized management through a familiar interface. This makes it an efficient choice for teams that want to consolidate their security tools and leverage their existing Microsoft investment for robust protection.
IBM Security
IBM Security is well-regarded for its focus on advanced data protection, particularly through sophisticated encryption methods. They offer a broad range of security solutions and services centered on data security, threat detection, and incident response. IBM’s approach often involves leveraging artificial intelligence, like their Watson platform, to analyze threats and automate security operations. This makes them a solid partner for large organizations and enterprises that handle sensitive data and require advanced capabilities to manage complex security challenges and respond to incidents with speed and precision.
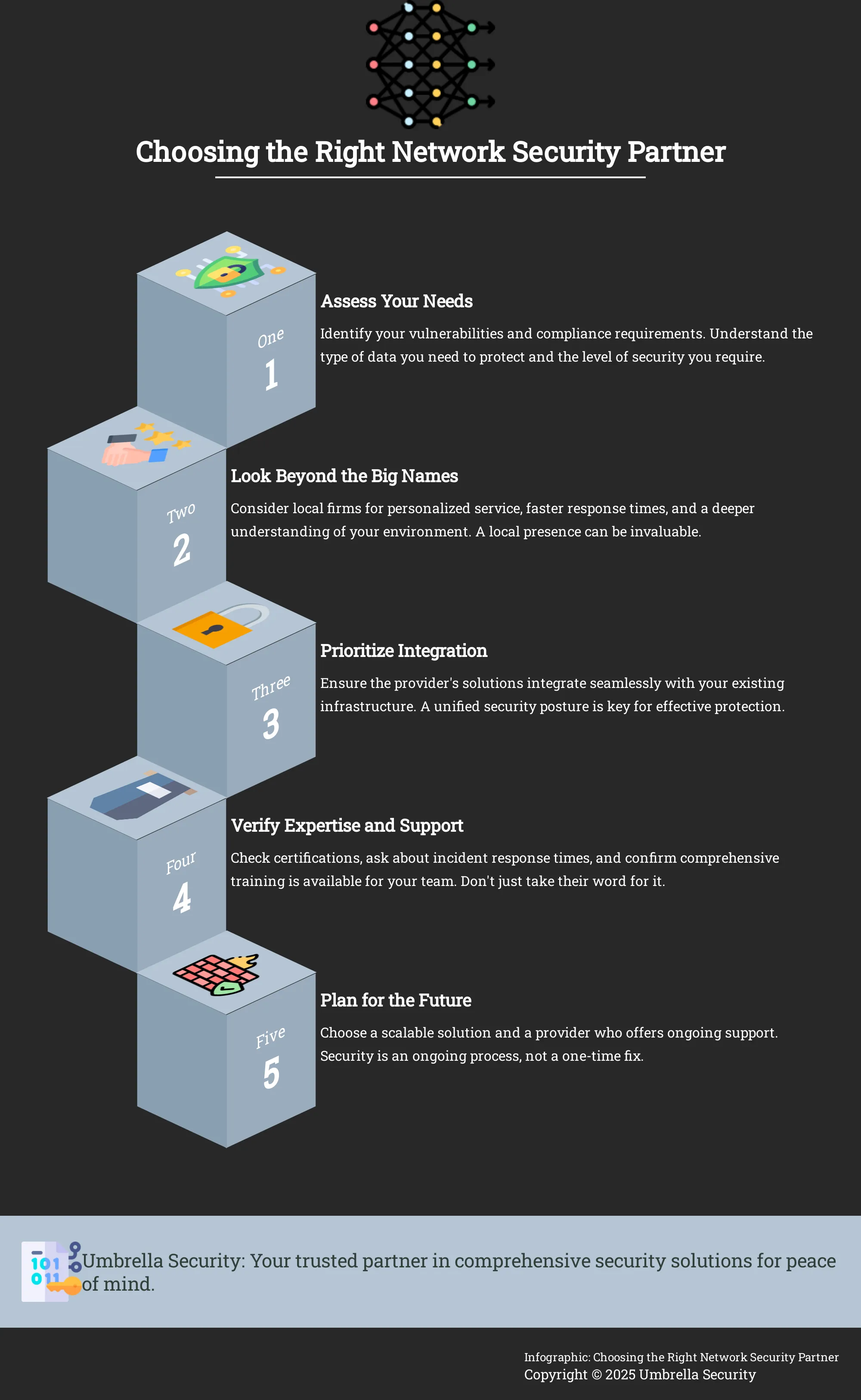
How to Choose the Right Network Security Provider
Selecting a network security partner is a major decision. You’re not just buying a product; you’re entrusting a company with the safety of your data, operations, and reputation. The right provider acts as an extension of your team, offering expertise and support that helps your business thrive securely. As you evaluate your options, it’s helpful to have a clear framework for what to look for. Moving beyond the sales pitch and digging into a company’s capabilities, processes, and track record will help you find a partner who truly fits your needs. Use the following criteria as a checklist to guide your conversations and make a confident, informed choice for your Chicago business.
Verify Their Technical Expertise and Certifications
Before you trust a provider with your network, you need to confirm they have the right skills for the job. Look for a team whose technicians hold respected industry certifications. Credentials like the Certified Information Systems Security Professional (CISSP) or Certified Information Security Manager (CISM) aren’t just acronyms; they represent a deep, verified understanding of security principles and practices. A certified team is more likely to be current on the latest threats and technologies. Don’t hesitate to ask about the team’s qualifications and ongoing training. This ensures you’re partnering with genuine experts who are committed to their craft and capable of designing and maintaining a truly secure environment for your business.
Review Their Customer Support and Training
Great technology is only effective if your team knows how to use it and has support when things go wrong. A top-tier security provider doesn’t just install a system and disappear. They should offer comprehensive training to get your staff comfortable with new tools and processes. Equally important is their customer support model. Are they available 24/7? What are their typical response times? A strong partner will offer ongoing support and act as a resource for any questions you have. This commitment to service ensures your access control systems and other security measures are always working for you, not against you.
Check Their Integration Capabilities
Your security tools shouldn’t operate on separate islands. For a security strategy to be effective, its components must work together seamlessly. A critical question for any potential provider is how their solutions will integrate with your existing infrastructure. Can their security camera systems communicate with your access control logs? Will their network alerts feed into your current IT management software? A provider focused on integration can create a unified security posture that provides greater visibility and control. This approach eliminates dangerous blind spots that can arise when systems don’t communicate, giving you a much stronger, more cohesive defense.
Ask About Response Times and Incident Management
When a security breach occurs, every minute matters. A slow response can be the difference between a minor issue and a catastrophic event. That’s why it’s essential to understand a provider’s incident management process before you sign a contract. Ask them to walk you through their plan: How do they detect and verify a threat? What are the immediate steps they take to contain it? What are their guaranteed response times, often outlined in a Service Level Agreement (SLA)? A provider with a well-defined and practiced incident response plan, like an mass emergency notification system, demonstrates they are prepared to act decisively when you need them most.
Evaluate the Cost Structure and ROI
While budget is always a factor, the cheapest option is rarely the best when it comes to security. Instead of focusing solely on the initial price tag, evaluate the total cost of ownership and the potential return on investment (ROI). A quality security solution is an investment in business continuity. Consider the immense costs associated with a data breach, including downtime, regulatory fines, and damage to your reputation. A reliable security provider helps you avoid these costs, delivering a significant ROI. Ask for a clear breakdown of all fees—including installation, licensing, and ongoing support—to ensure there are no surprises and that the value aligns with your investment.
Ensure They Meet Compliance Standards
For many Chicago businesses, especially in sectors like healthcare, finance, or cannabis, adhering to strict regulatory standards is non-negotiable. Failing to comply with regulations like HIPAA or PCI DSS can lead to severe penalties. Your security provider must have a deep understanding of the specific compliance requirements for your industry. Ask them how their solutions and services will help you meet and maintain these standards. A knowledgeable partner will be able to configure systems and generate reports that simplify your audit processes, turning a complex legal obligation into a manageable part of your security routine.
Confirm Asset Visibility and Management
You can’t protect what you can’t see. A fundamental part of any strong security strategy is having a complete and accurate inventory of every device, user, and application on your network. Ask potential providers how their tools improve asset visibility. They should offer solutions that automatically discover and map your entire network, from servers and laptops to IoT devices like security cameras or specialized sensors. This comprehensive view allows you to spot unauthorized devices, identify unpatched software, and manage vulnerabilities proactively. Enhanced visibility, including tools like an air, light, and sound detection sensor, is the foundation of effective risk management.
Core Security Services and Technologies to Expect
When you partner with a network security company, you’re not just buying a product; you’re investing in a comprehensive strategy. A top-tier provider will offer a suite of services and technologies designed to work together, creating multiple layers of defense for your organization. From foundational tools to advanced, AI-driven platforms, these core components are what you should look for. They represent the modern standard for protecting your digital assets, ensuring your business is prepared for the complexities of today’s threat landscape. Understanding these services will help you have more productive conversations with potential providers and choose a partner who can truly meet your security needs.
Firewall Protection and Management
Think of a firewall as the digital gatekeeper for your network. It stands between your internal network and the outside world, monitoring incoming and outgoing traffic and deciding what to allow or block based on a set of security rules. But simply having a firewall isn’t enough. Firewall misconfigurations are a frequent source of vulnerability, which is why professional management is so important. An expert team will ensure your firewall is correctly configured, updated, and monitored, providing a strong first line of defense against unauthorized access and malicious activity. This continuous oversight is critical for adapting to new threats and keeping your network secure.
Intrusion Detection Systems
While a firewall blocks known threats at the perimeter, an Intrusion Detection System (IDS) acts as a security guard inside your network. It actively monitors network traffic for suspicious activity or policy violations. If an IDS spots a potential threat, it sends an alert to your security team for investigation. This is a key part of a multi-layered security approach that combines technical controls with active monitoring. An IDS gives you the visibility you need to identify and respond to potential attacks in real-time, catching threats that might otherwise slip through the cracks.
Endpoint Security Solutions
Every device connected to your network—from laptops and servers to smartphones and even IoT devices like security camera systems—is an endpoint. Each one is a potential entry point for an attack. Endpoint security solutions are designed to protect these devices from malware, ransomware, and other threats. These platforms go beyond traditional antivirus software, offering more advanced detection and response capabilities. With a high user satisfaction rating, Endpoint Protection Platforms are considered an essential part of any comprehensive security strategy, securing the devices where your employees work and your data resides.
Cloud Security Services
As more businesses move their operations and data to the cloud, securing these environments has become a top priority. Cloud security involves a set of policies, controls, and technologies designed to protect cloud-based infrastructure, applications, and data. Organizations that rely on cloud services face unique challenges, including the risk of data breaches and unauthorized access. A quality security provider will offer specialized cloud security services to help you configure your cloud environment securely, manage access, and protect your data, whether you’re using a public, private, or hybrid cloud model.
AI and Machine Learning Applications
Cyber threats are constantly changing, and human security teams can’t always keep up. This is where artificial intelligence (AI) and machine learning (ML) come in. These technologies are transforming cybersecurity by automating threat detection and response. AI plays a significant role in modern security solutions by analyzing massive amounts of data to identify patterns and anomalies that could indicate an attack. This allows security systems to spot new and emerging threats much faster than traditional methods. By automating routine tasks, AI also frees up your security professionals to focus on more complex strategic initiatives.
Zero Trust Security Implementation
The traditional security model of a strong perimeter with a trusted internal network is no longer effective. The Zero Trust model operates on a simple principle: never trust, always verify. This approach assumes that threats can exist both outside and inside the network. Under a Zero Trust framework, no one is trusted by default, and verification is required from everyone trying to gain access to resources. This focus on strict access controls and continuous verification of users and devices is a vital strategy for minimizing risk. It’s a fundamental shift in security thinking that helps protect against both external attacks and insider threats.
Extended Detection and Response (XDR)
As security tools multiply, it can be difficult to get a clear, unified view of your security posture. Extended Detection and Response (XDR) platforms solve this problem by collecting and correlating data from multiple security layers—including endpoints, cloud services, and networks. This provides a more holistic view of potential threats, allowing for faster and more effective incident response. Many leading companies are offering combined solutions like XDR that cover many security needs at once. An XDR approach breaks down security silos, giving your team the context they need to understand the full scope of an attack and respond decisively.
Overcoming Common Implementation Hurdles
Putting a new network security plan into action is a big step, and it often comes with its own set of challenges. From budget constraints to integrating new tech with old systems, these hurdles can feel daunting. But with a clear strategy, you can clear them smoothly. The key is to anticipate these common issues and plan for them from the start. Let’s walk through some of the most frequent obstacles and how you can approach them effectively.
Manage Your Resources and Budget
Implementing a robust security system is an investment, and it’s important to treat it as one. Many organizations find their resources and budgets strained, especially when dealing with the complexities of cloud services and the constant threat of data breaches. The first step is to get a realistic picture of your needs and the associated costs. A good security partner can help you understand where your money is best spent, ensuring you get a system that protects you without unnecessary expenses. This isn’t just about buying software; it’s about investing in your company’s resilience and future.
Integrate with Existing Systems
Your business already has a unique digital ecosystem. A new security solution can’t just be dropped in; it needs to integrate seamlessly with your existing network architecture, data flows, and access controls. A poorly integrated system can create new vulnerabilities or disrupt your operations. Before you begin, it’s crucial to map out your current infrastructure. Working with a specialist in system integration ensures that all your components—from cameras to access points—work together as a single, cohesive unit, strengthening your overall security posture from day one.
Prioritize User Training and Awareness
You can have the most advanced security technology in the world, but it won’t be effective if your team isn’t prepared. Human error remains one of the biggest security risks, as many cyberattacks begin by targeting employees. That’s why comprehensive user training is non-negotiable. Your staff needs to understand the new systems and, more importantly, recognize potential threats like phishing emails or social engineering tactics. Building a culture of security awareness turns your team from a potential vulnerability into your first line of defense, making everyone a part of the solution.
Keep Pace with New Threats
The world of cybersecurity is anything but static. Attack methods are constantly evolving, which means your defense strategy can’t be a “set it and forget it” project. Staying protected requires continuous vigilance and adaptation. This is where a dedicated security partner becomes invaluable. They stay on top of emerging threats and ensure your systems are always updated to handle the latest challenges. This proactive approach means you can focus on your business, confident that your security camera systems and other defenses are prepared for whatever comes next.
Consolidate Your Security Tools
Many businesses accumulate a patchwork of different security tools over time, each addressing a specific issue. While well-intentioned, this can lead to a complicated and inefficient system with potential security gaps between tools. Combining your networking and security into a unified platform makes your defenses stronger and much easier to manage. By consolidating your tools, you gain a clearer, more comprehensive view of your security landscape. This integrated approach simplifies management for your IT team and reduces the chances of something slipping through the cracks.
Plan for Scalability
Your business is going to grow, and your security system needs to be ready to grow with it. A solution that works for you today might not be adequate in a few years. When choosing a security provider, think about your long-term goals. Will you be adding new locations, hiring more employees, or adopting new technologies? An integrated and scalable system, built on a solid foundation like a modern fiber network, will adapt to your changing needs, saving you from costly overhauls down the road.
Develop a Security Investment Roadmap
Making security decisions on an ad-hoc basis can lead to wasted resources and an ineffective strategy. Instead, it’s better to develop a long-term security investment roadmap. This strategic plan outlines your security goals and the steps needed to achieve them over time. It helps you simplify your security stack, improve performance, and protect your data as your business evolves. Working with a security consultant to build this roadmap ensures your investments are strategic, purposeful, and aligned with your company’s growth and security needs.
How to Measure Your Security’s Success
Once you’ve partnered with a security provider and implemented new systems, how do you know if they’re actually working? Measuring the success of your security strategy goes beyond simply counting the incidents you’ve prevented. It’s about understanding your risk, demonstrating value to stakeholders, and making smarter decisions for the future. Without clear metrics, you’re essentially flying blind, unable to justify your budget or prove that your investments are paying off. This is especially critical when you need to communicate the importance of security to leadership who may not be fluent in technical jargon.
A structured approach to measurement helps you move from a reactive to a proactive security stance. It allows you to identify weak spots before they become major problems and to fine-tune your defenses as new threats emerge. By tracking the right data, you can tell a clear story about your security’s impact on the entire organization, from protecting critical assets to ensuring operational continuity. The following steps will help you build a framework for evaluating your security measures effectively, ensuring they align with your overall business goals and provide a real return on investment.
Define Your Key Performance Indicators
Before you can measure success, you need to define what it looks like for your organization. Establishing clear Key Performance Indicators (KPIs) is the first step. These aren’t just technical jargon; they are the specific, measurable goals that connect your security efforts to your business objectives. Think about what matters most. Is it reducing the time it takes to detect a threat? Minimizing system downtime? Or perhaps lowering the number of successful phishing attempts? Your KPIs should be tailored to your unique environment and risks. Common examples include Mean Time to Detect (MTTD), Mean Time to Respond (MTTR), the percentage of critical vulnerabilities patched within a set timeframe, and the number of policy violations. By setting these benchmarks, you create a clear standard for performance.
Assess Your Security Posture
You can’t measure improvement without knowing your starting point. A thorough assessment of your security posture is crucial for identifying vulnerabilities and ensuring your defenses are robust. This process gives you a comprehensive baseline of your current security health. It involves mapping your network architecture, understanding data flows, and reviewing who has access to what. This evaluation should combine automated scanning tools with manual testing to uncover potential weaknesses in your systems, from outdated software to misconfigured access control systems. The goal is to get a complete picture of your vulnerabilities so you can prioritize fixes and focus your resources where they’ll have the greatest impact. This initial assessment becomes the benchmark against which all future improvements are measured.
Create a Strategy for Continuous Improvement
The security landscape is constantly changing, which means your defense strategy can’t afford to stand still. Threats evolve, new vulnerabilities are discovered, and your business needs shift. That’s why developing a strategy for continuous improvement is vital to adapt to the evolving threat landscape. Your security program should be a living, breathing part of your organization, not a one-time project. Use the data from your KPIs and security assessments to create a feedback loop. When you identify a weakness, create a plan to address it. When you meet a goal, set a new, more ambitious one. This cycle of measuring, analyzing, and refining ensures your security measures remain effective and relevant. It’s about making incremental, data-driven adjustments that strengthen your overall security posture over the long term.
Track Your Risk Management Metrics
Ultimately, security is about managing risk. Tracking your risk management metrics helps you translate technical data into a language that resonates with business leaders: impact and cost. This involves looking beyond individual incidents to understand the broader financial and operational implications of your security initiatives. Metrics like the cost per incident, the financial impact of downtime, or the rate of compliance failures can paint a powerful picture. A comprehensive network security assessment helps you continuously monitor these metrics. By tracking them over time, you can demonstrate how your security investments are reducing the organization’s overall risk exposure. This not only helps justify your budget but also guides future strategic decisions, ensuring your security program is always aligned with the company’s bottom line.
Related Articles
- Best Commercial Security Packages: Features & Pricing – Umbrella Security Systems
- Top Office Building Security Systems: Features & Comparison – Umbrella Security Systems
- IoT Security Solutions: A Guide for Businesses – Umbrella Security Systems
- How to Choose Security Integrators in Chicago – Umbrella Security Systems
Frequently Asked Questions
My business already has an IT department. Why do I need a separate network security company? Think of it this way: your in-house IT team are the brilliant general practitioners who keep your entire technology ecosystem healthy and running smoothly day-to-day. A dedicated security partner, on the other hand, is a team of specialists, like cardiologists or immunologists. Their sole focus is on anticipating, identifying, and neutralizing complex threats. They live and breathe security, which allows them to provide a level of proactive defense and specialized expertise that complements your IT team’s essential work.
You listed several big national companies. What’s the advantage of working with a local Chicago-based firm? While large national providers offer powerful platforms, a local partner provides a level of hands-on service and integration that is hard to match from a distance. A Chicago-based firm understands the local business landscape and can be on-site to ensure your systems are implemented and integrated perfectly within your specific environment. This creates a true partnership where you have direct access to the experts designing and managing your security, rather than just being another account number.
What does it mean to integrate physical security with network security? Integrating physical and network security means your security systems can talk to each other to create a smarter, more complete picture of what’s happening. For example, if your access control system logs an unauthorized attempt to enter a server room, it can automatically trigger an alert on your network, flag the user’s digital activity as high-risk, and point a security camera to that door. It connects the dots between the physical world and your digital infrastructure, turning isolated events into actionable intelligence.
How can I justify the cost of a professional security service to my leadership team? The best way to frame the conversation is to shift the perspective from an expense to an investment in business continuity. Compare the cost of a proactive security partnership against the potential cost of a single breach, which includes not just financial loss but also operational downtime, regulatory fines, and long-term damage to your company’s reputation. A strong security posture isn’t a line item; it’s a foundational element that protects the entire business from catastrophic risk.
What is the single most important first step to improving my company’s security? The most crucial first step is getting a clear and honest understanding of where you currently stand. You can’t effectively protect what you can’t see. A professional security assessment will give you a comprehensive baseline of your vulnerabilities, from unpatched software to gaps in your physical access. This provides a detailed roadmap that shows you exactly where to focus your resources for the greatest impact, ensuring your security investments are strategic and effective from day one.